This admin procedure will provide background information on utilizing the Vulnerability Management section to view exposure that exists on registered devices.
This article is intended for employees of organizations that use Sittadel's security. Additionally, there are some actions that can only be accomplished by those with administrative privileges.
Managing Vulnerabilities
Managing vulnerabilities within the organization is a key tenant to ensuring the security of Windows devices. While many people hone in specifically on Windows updates and patches, there is more to the story that should not be ignored. Just like Windows needs patches to address discovered vulnerabilities, applications on the device may also develop their own vulnerabilities over time and need to be updated to versions where the vulnerability is removed. A note to this is that devices onboarded as Corporate Devices will have vulnerability information available, while Personal Devices will not show vulnerability information.
This guide will accomplish the following:
- View the Vulnerability Dashboard
- Investigate Open Vulnerabilities
- Exceptions for Vulnerabilities
- Remediate Open Vulnerabilities
Applicable Scope: Administrators
Required Group Membership: Admin.Vulnerability
View the Vulnerability Dashboard
- Navigate to Vulnerability Dashboard – O365 Defender, this area houses the overview of all vulnerability management items in the organization. This summary can be used to highlight the vulnerability management progress over time for upper management, determine the highest risk devices, and determine the highest risk software.

Investigate Open Vulnerabilities
- Navigate to Recommendations – O365 Defender, this page shows all the recommendations for devices, including both configuration and software recommendations. To find application specific recommendations, click the Filter option.
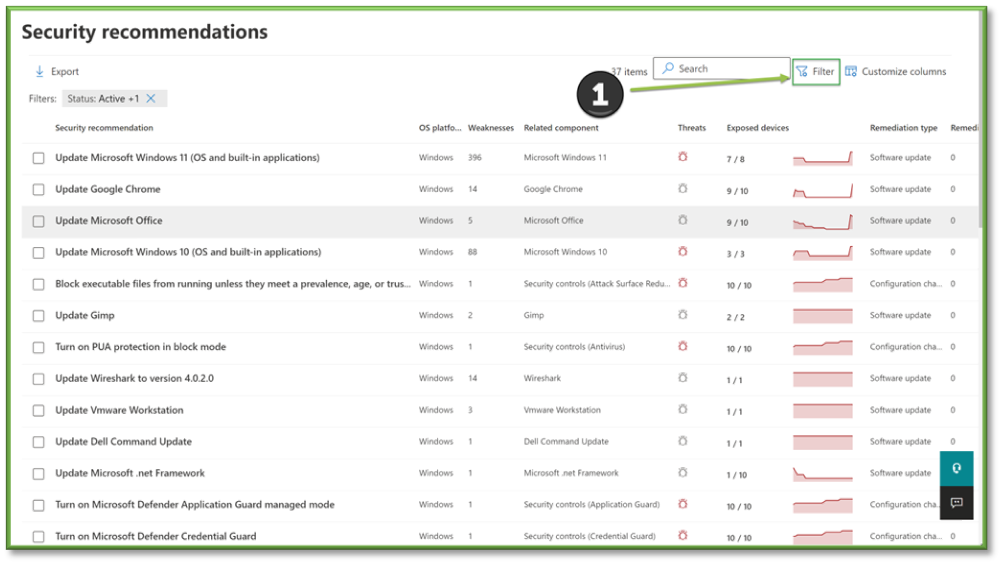
- In the filter prompt, for the Remediation Type select Software Update, Software Upgrade, and Software Uninstall. Click Apply.
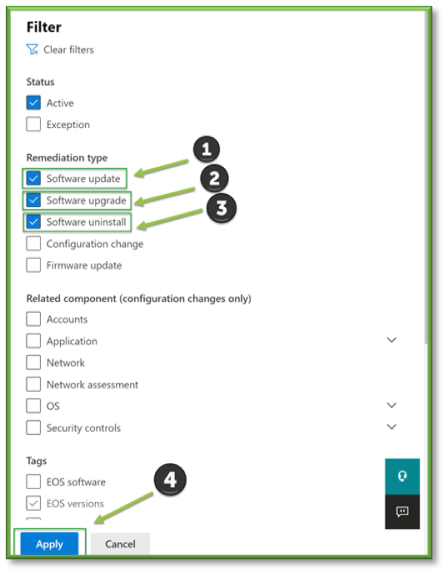
- Look over the list of applications. When analyzing the list, hone in on the Threats column. Not all vulnerabilities are created equal, and while some may exist in the wild, they are not always being actively exploited. Microsoft understands this, and uses the icons as follows:

- Indicates that a publicly available exploit is available. As the red would suggest, these are higher priority.
 - Indicates there are no public exploits available. As grey would suggest, these are lower priority.
- Indicates there are no public exploits available. As grey would suggest, these are lower priority. -
When managing vulnerabilities, it is virtually impossible to have zero. It is more of a delicate balance between time spent remediating and keeping up versus the risk it addresses. Thus, it is up to the organization how much they wish to prioritize smaller vulnerabilities and whether the risk outweighs the time spent remediating. If the risk is low, an exception stating so may be made. If the risk is high, remediation may be in order.
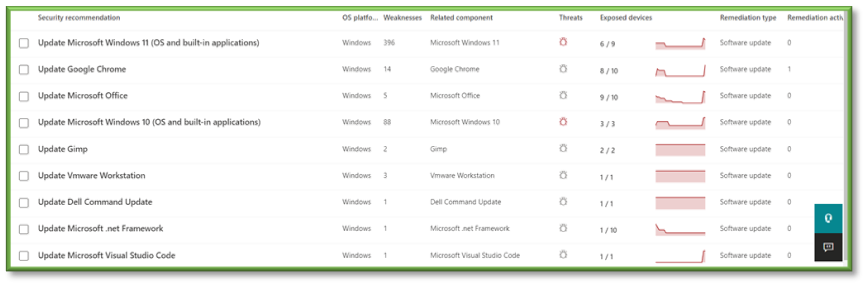
- Select one of the applications from the list. Upon clicking into one, the Description will be displayed to show what must be done. In this case, we need to ensure Chrome is updated to the latest version.

- As we touched on earlier, when it comes to vulnerabilities the two options we have are to:
- Make an exception and accept the risk it poses – Move to the Exceptions for Vulnerabilities
- Remediate and remove the vulnerability – Move to the Remediate Open Vulnerabilities
Exceptions for Vulnerabilities
- With the application checked, select Exception Options, enter the Justification for why, provide Context in case the decision is reviewed at a later date, set the Duration for how long it will be exempted for, and click Submit. The vulnerability has been closed as an exception.

Remediate Open Vulnerabilities
If a software vulnerability is identified and after investigation determined to not be in scope for an exception, remediation is the next step. To remediate a vulnerability, following the recommendation given in the description on affected devices will lead to the vulnerability being remediated.
- With our vulnerability open, click the Exposed Devices tab. This will display a list of all affected corporate devices which are in scope for the vulnerability. We recommend that you analyze the Last Seen column to check for devices that have not been online for over 2 weeks. Devices offline for over 2 weeks can be reasonably assumed to be either unhealthy and requiring a re-enrollment, having changed names recently, or in need of being turned on again. Devices with name changes can be deleted from within the Devices tab. If the device has checked in recently, move to the next step.

- For active devices, one of two items have happened:
- For Windows Updates: The automatic updater has failed in some regard. It is recommended that the device is restarted, which can be initiated remotely as detailed in the Device Management Procedure. If a restart does not fix the issue, manual checking and installing updates via the Settings app on the endpoint is recommended. If none remediate the issue, a Fresh Start retaining user data as detailed in the Device Management Procedure may be a final resort.
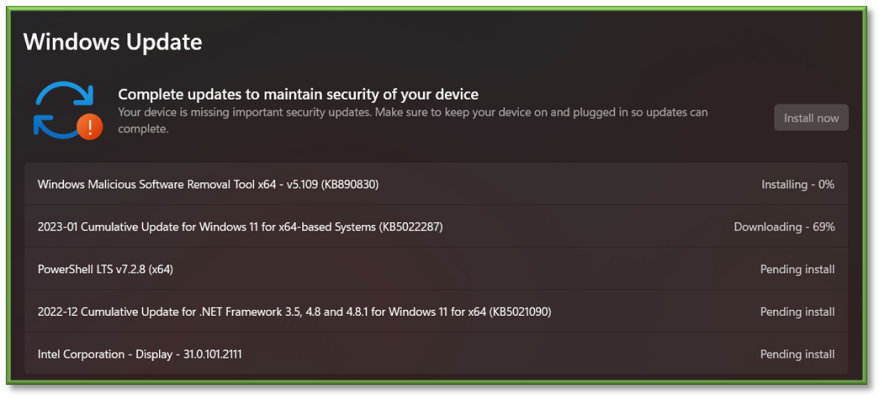
- For Application Updates: Some applications come with automatic updaters, while some do not. Check if the application in question has automatic updates turned on, or if they need to be installed manually.
- For Windows Updates: The automatic updater has failed in some regard. It is recommended that the device is restarted, which can be initiated remotely as detailed in the Device Management Procedure. If a restart does not fix the issue, manual checking and installing updates via the Settings app on the endpoint is recommended. If none remediate the issue, a Fresh Start retaining user data as detailed in the Device Management Procedure may be a final resort.
- Upon remediating the open vulnerability, the option should disappear within the console within 24 hours. If the vulnerability is not resolved, restart the device, or ensure the device is checking into Intune properly.
You're Finished!
You should have successfully viewed the vulnerability management section of the O365 Defender portal; if any high severity vulnerabilities have been identified, additional inspection will need to be conducted to determine a remediation process for the device. For any other problems or questions, reach out to us!
