This admin procedure will provide background information on important management sections tied to a user account, providing details on expected behavior and establishing guidelines that should be followed for constructing a baseline.
This article is intended for employees of organizations that use Sittadel's security. Additionally, there are some actions that can only be accomplished by those with administrative privileges.
Procedure Scope: Administrators
Required Group Membership: Admin.UserRole
Reviewing a User Account
- Navigate to Users – Azure Active Directory, locate the user you wish to view account information for.

- Before we traverse the user profile, we will conduct an initial user check for sign-in activity. This will be useful in determining if the account is live, if the account is not , it is best practice to disable the account until employment status can be checked to determine if account removal is allowed.
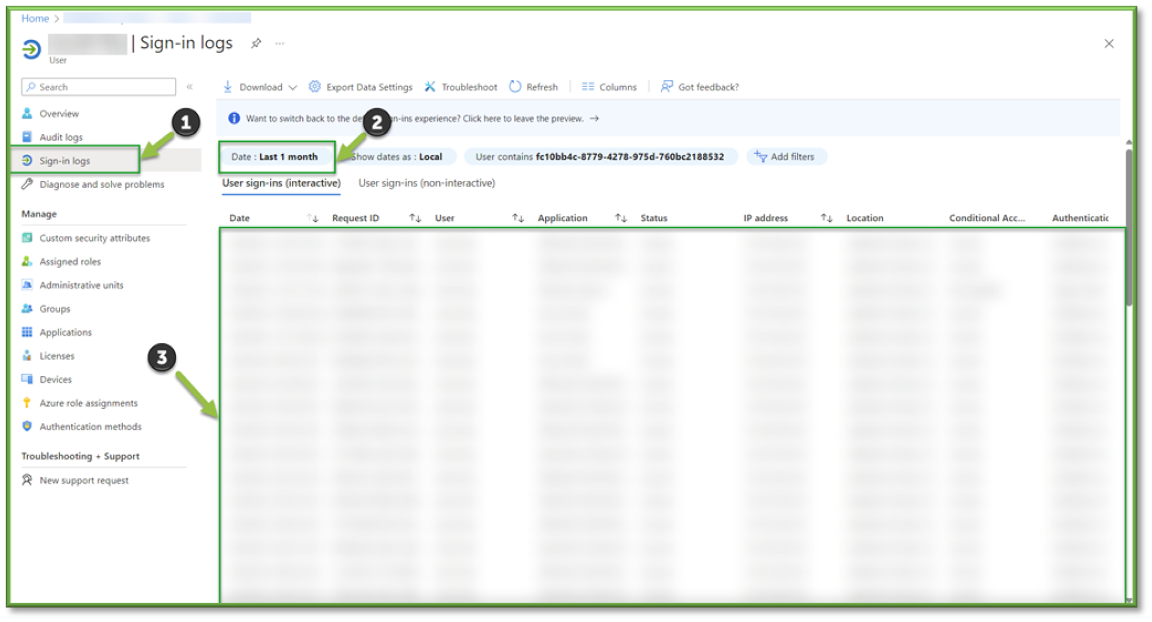
- Locate the Sign-In Logs section of the user profile, this will generate a report of all the recorded sign-in activity for the user with the appropriate filters configured for the specific profile you are interfacing with.
- Select the Date filter, specify 1 month and select Apply to change the filter specification.
- If no sign-in activity has been captured during the specified timeframe, proceed with disablement, and follow up on employment status for the listed user for possible account removal.
- To start off the account review process locate the Assigned Roles section of the user profile. This will list all the assigned roles associated with the account, detailing the type of permissions granted by the role as well as how the assignment was acquired via group or directly assigned from administration. These values are important to keep eyes on.
- If a discrepancy is detected in role assignment; make note of the role in question and follow up with management to determine if the role fits the need of the users job class. If the role is not necessary, then select the role and select Remove Assignments to remediate the privilege creep.

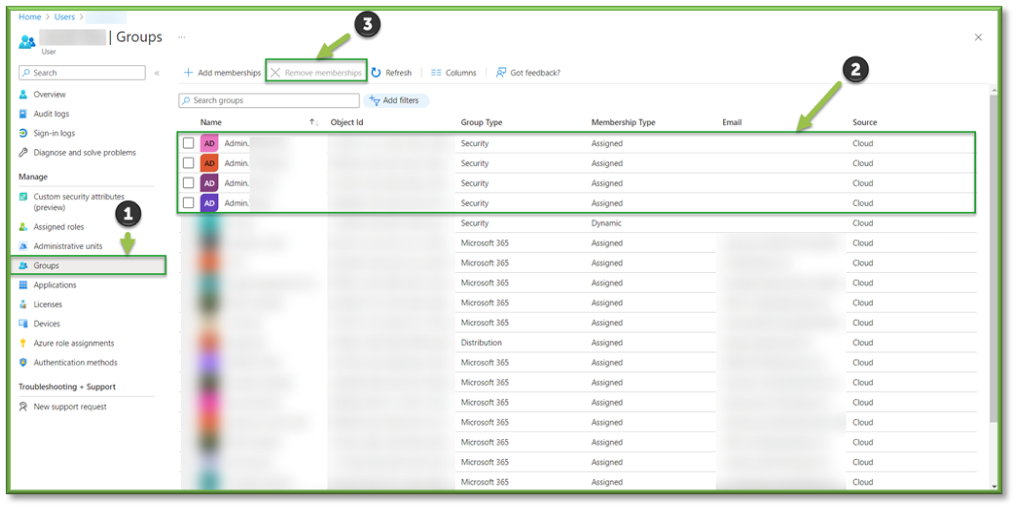
- Group Assignment will go hand in hand with Role Assignment, locate the Groups section of the user profile to begin searching for privilege creep. A list of all assigned groups will be generated, it is important to make note of all Admin.xxx groups the user is included in.
- A reference to the user’s job-related task will determine if the user is over assigned group permissions, this will also be reflected in the Assigned Roles section by the Assignment Path column.
- If a user is outside of the scope of their group assignments; make note of the group in question and follow up with management to determine if the users job class has taken on any additional task that haven’t been reflected. If no additional role specific tasks have changed, select the group in question and select Remove Memberships to remediate the privilege creep.
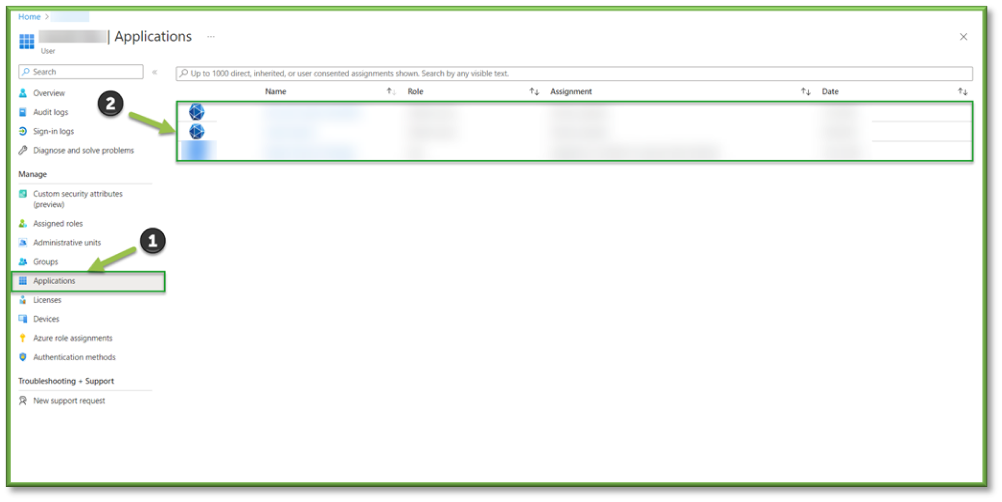
- Application Assignments could play a role in users being able to view organizational information that is outside the realm of what their job classification allows. Locate the Applications section of the user profile to begin searching for privilege creep. A list of all the applications a user is assigned to will be displayed.
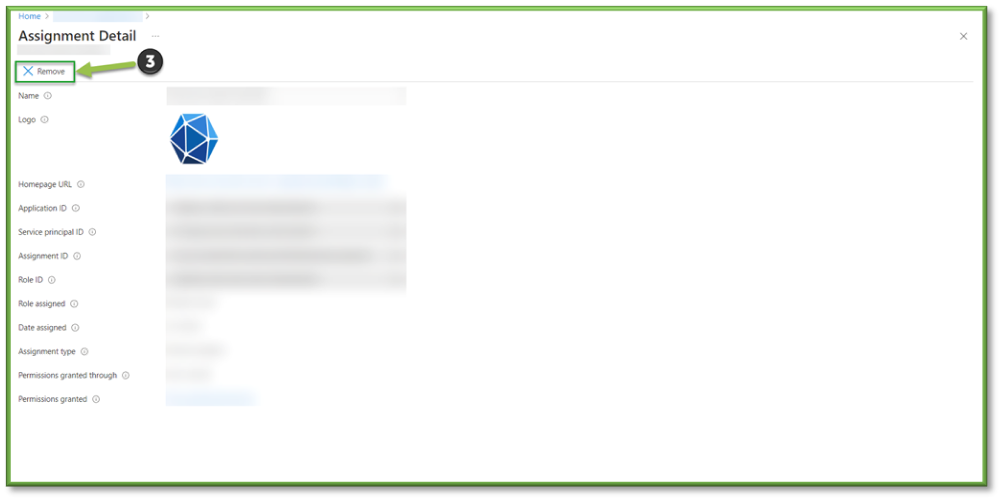
- If you see an application that a user shouldn’t be assigned; make note of the application in question and follow up with management to determine if the users job class entitles them access to the application. If not, select the app in question and select remove to alleviate the data access encroachment.
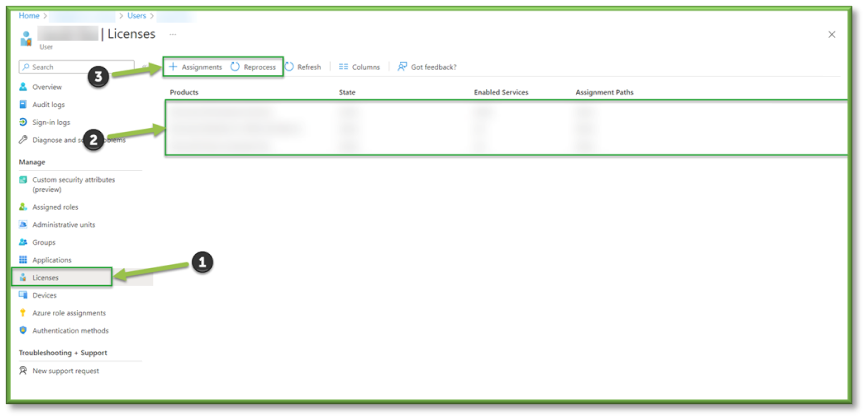
- Licensure plays an important role in user access, locate the Licenses section of the user profile. A variety of different issues can arise from licensing.
For starters if a user doesn’t have the proper licensure, they will be unable to have proper security policy pushed on them due to the discrepancy between setting licensure requirements and the licensure the user possesses.
Additionally, if a user possesses a license that is outside of the scope of what is required for their job, that is an unnecessary cost that is being applied to the organization at a monthly or annual rate. - If a user is deficient in a license, select Assignments to apply a proper license to the account. If a user is consuming an unnecessary license, select Reprocess after the removal of the license has taken place to force a licensing check from Azure.
- Devices can also be viewed from a user account, locate the Devices section of the user profile to see all devices associated with a user.
- This can be useful in determining non-compliant devices that might pose a possible security risk to the organization. Additionally, you can make device status changes from this window which can be useful in the case of incident response or user on/off boarding.

- Authentication Methods can be useful in determining issues related to user MFA, locate the Authentication Methods section of the user profile.
- From this window you can push a Password Reset for the end user in the case of a request or a compromised credentials situation.
- Additionally, you can reconfigure an MFA registration to the authenticator app upon request or Revoke any current sessions authenticated with MFA during a compromised access circumstance.

You're Finished!
You should have successfully reviewed your first account, take into account that this review process is necessary in keeping up with the enforcement of organizational policies related to carrying out the principals of least privilege on user accounts, reducing the exposure risk for inactive accounts and making sure that users are in line with the baseline establishment of application deployments and security features tied to minimum licensure. For any other problems or questions, reach out to us!
