This admin procedure will provide background information on viewing Sign-In logs for Azure AD tied programs, along with some important filters that will aid in determining legitimate log in attempts.
This article is intended for employees of organizations that use Sittadel's security. Additionally, there are some actions that can only be accomplished by those with administrative privileges.
Procedure Scope: Administrators
Required Group Membership: Admin.UserSecurity
Reviewing User Sign-In Attempts
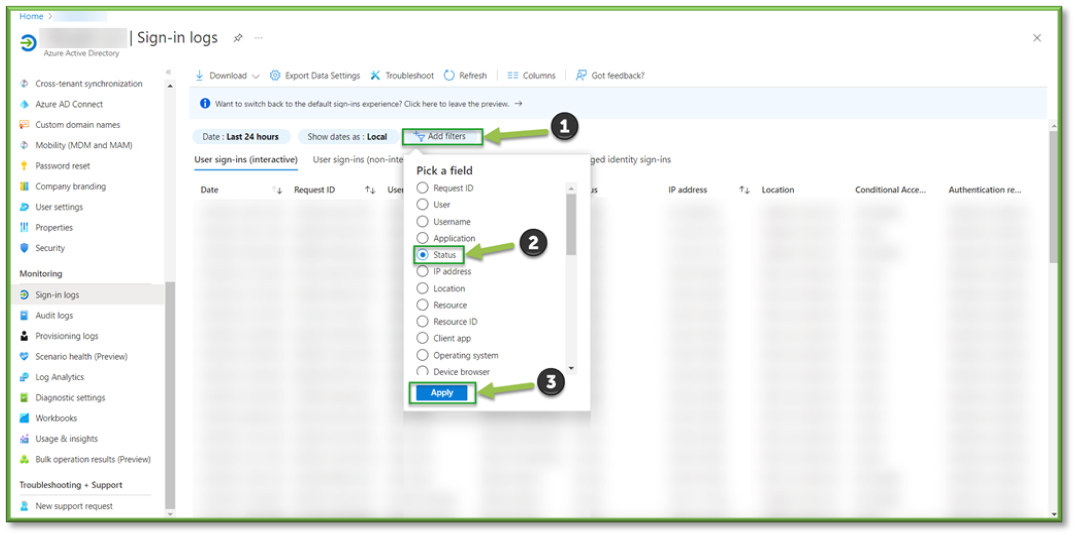
- Navigate to Sign-In Logs – Azure Active Directory, select Add Filters. Locate the Status filter and select Apply.
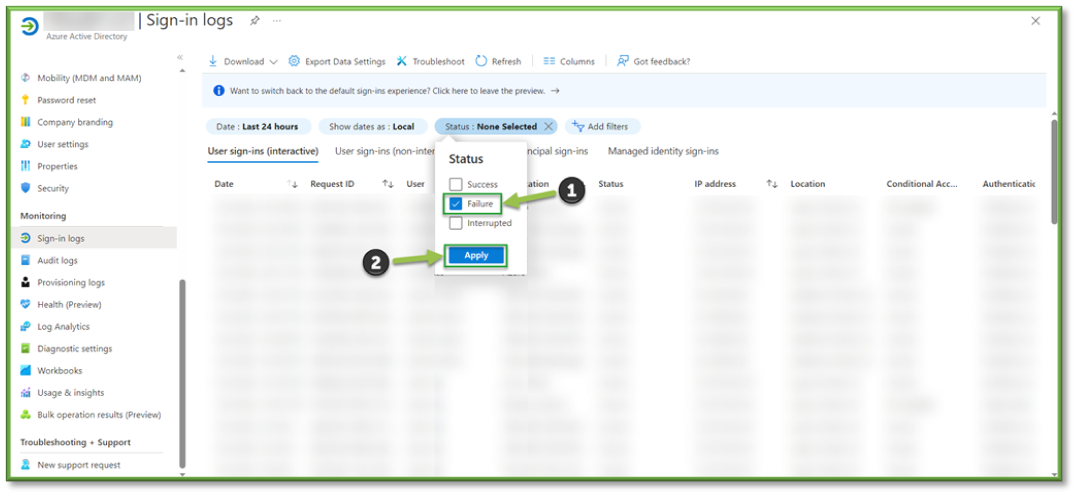
- Select the Status filter, locate the Failure filter and select Apply.
- A list of all failed user sign-ins will be generated, select the failed sign-in in question. A pop-up will display additional troubleshooting information. The first section we will look at will be Basic Info this will display information associated with the failure, who committed the fault and an explanation of what caused the failure. This can help determine which user it is, whether this failure should be escalated to a more serious threat, and if it a simple failure being caused or if it is a possible policy misconfiguration causing the outage.

- The Location tab will be useful in determining if the device location is coming from the proper user. If the company is based out of Florida and the user works locally; it will be easy to identify if this is a spoofed login attempt and the failure was due to stolen credentials halted by a missed MFA prompt. Additionally, the Trusted Locations definition will be applied here, depending on the countries selected if the device location falls outside of scope that will be a likely cause of failure as well.

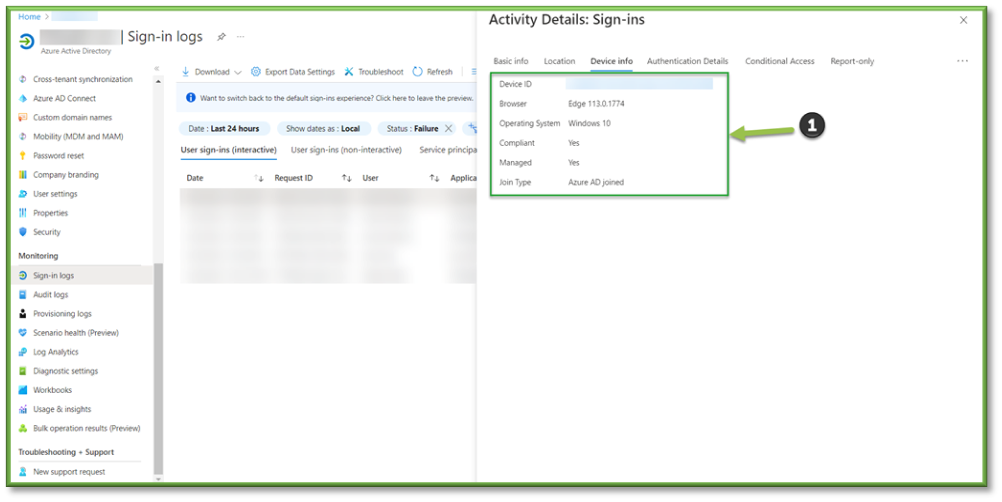
- The Device Info tab will allow you to see the device associated with the user login. If the device isn’t registered in Intune but it is trying to access the organizational tenant or resources that will be an expected failure due to non-compliance or it could be another sign of a spoofed sign in using stolen credentials.
- The Authentication Details tab will allow you to see if any form of authentication properties preconfigured for the user account could be causing the failure; additionally, any conditional access policies that relate strictly to authenticating will also be displayed along with a success/failure indicator which could point to additional misconfiguration of policy which might need remediation to allow proper access.

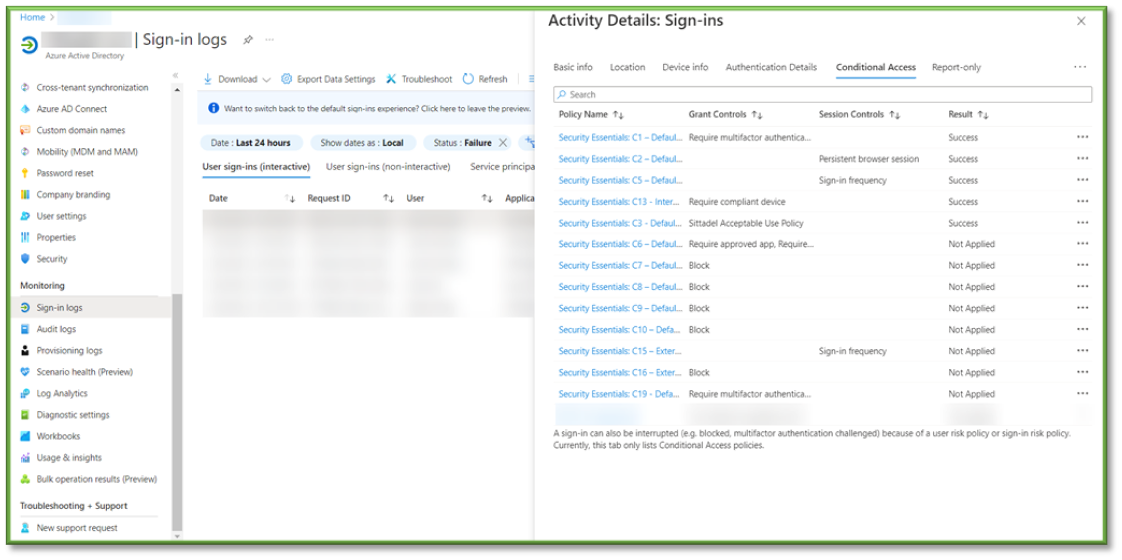
- The Conditional Access tab will show you all the conditional access policies configured to take place upon user authentication. Not all policies are applied based on user group assignment, but this could be an indicator of misconfiguration of a policy cause the failure or could be used as supplemental material to the user to have them remediate the issue on their end prior to authenticating.
You're Finished!
You should have successfully investigated your first log-in audit log; this area will be useful in troubleshooting end-user that are having issues with authenticating, as well as investigating an account that is potentially compromised. For any other problems or questions, reach out to us!
