This admin procedure will provide additional background information on the Reports section of the 365 Defender portal; breaking down general information that will be useful for possible security setting configuration remediation.
This article is intended for employees of organizations that use Sittadel's security. Additionally, there are some actions that can only be accomplished by those with administrative privileges.
Endpoint Security
As with many cybersecurity toolsets, the antivirus capabilities are one of the prime offerings included for protecting the device. While typical antivirus focuses solely on detecting the presence of malicious files, the Defender offering goes deeper to analyzing some actions to make for more comprehensive security beyond just the hash of the file. There are many facets of endpoint devices which should be monitored and response to if the situation arises. Using the monitoring areas below, the business will be able to stay on top of the alerts generated by security controls and ensure business continues smoothy.
To use the guide, follow the hyperlinks for each reporting metric, which lead to the URL containing the report.
This guide will cover monitoring in the following reporting blades:
- Incidents Dashboard
- Security Report
- Threat Protection
- Device Health
- Vulnerable Devices
- Web Protection
- Firewall
- Device Control
- Attack Surface Reduction Rules
Procedure Scope: Administrators
Required Group Membership: Admin.DeviceSecurity
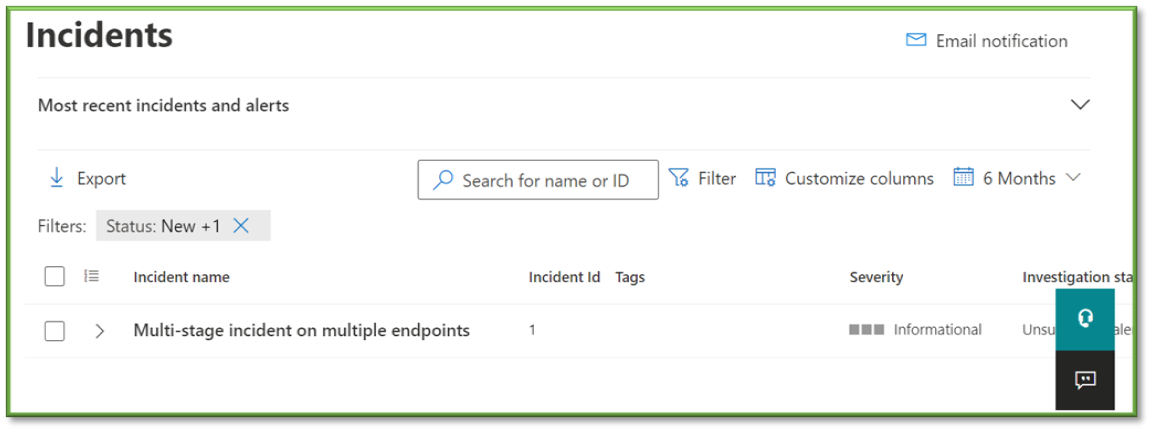
Incidents Dashboard
Description: View the incidents that have been identified by Microsoft Defender.
Metrics and Importance: High – Shows an overview of critical alerts and data that have been correlated into high-fidelity incidents. Metrics of interest include:
- Open Defender Incidents – Shows only the incidents which are of the Active or In Progress Any incidents that have been closed are not shown. Items in this list are of high importance, and upon locating one, the Defender Endpoint Incident Response Procedure should be followed.

Security Report
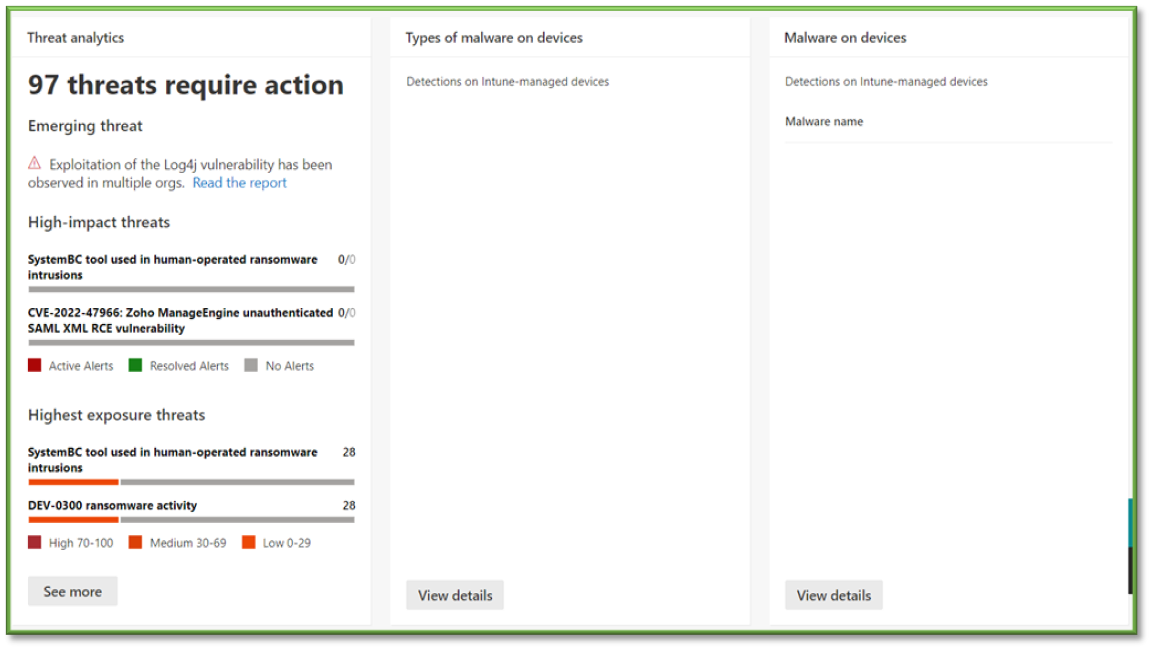
Description: View security trends and track the protection status of your identities, data, devices, apps, and infrastructure.
Metrics and Importance: High – Shows an overview of all security reporting into one tab. Metrics of interest include:
- Malware on devices – If malware is detected, a remediation must be done on the device. Remediation activities will vary based on the type of malware, but the first step should be to follow the Defender Endpoint Incident Response Procedure. If this is truly an emergency and you think there is legitimate concern, contacting Sittadel may be the best way to remediate.

Threat Protection
Description: See details about the security detections and alerts in your organization.
Metrics and Importance: Low – Shows an overview of all security settings, possibly for an executive level summary. No metrics are critical for monitoring here.

Device Health
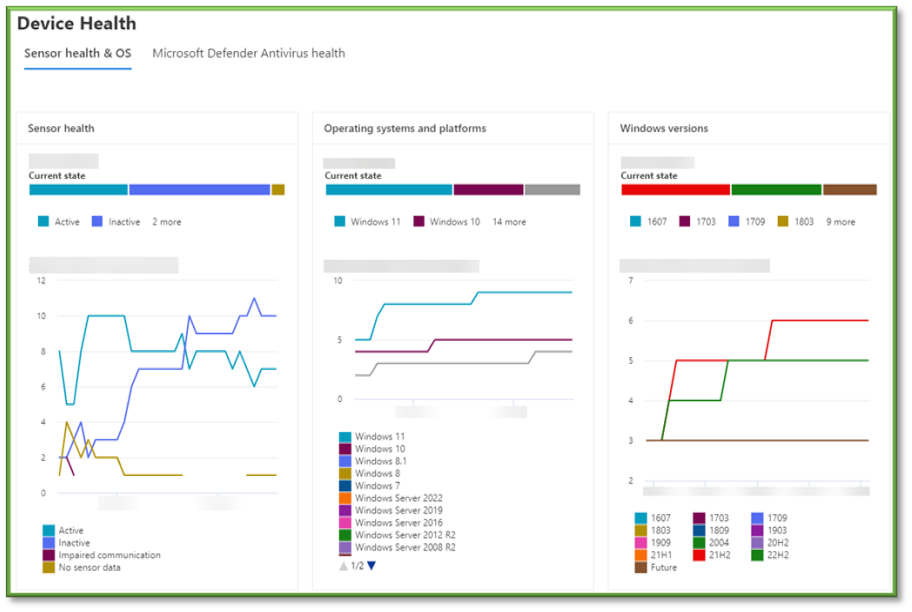
Description: Monitor device health, antivirus software status, operating system platform, and Windows 10 version if applicable.
Practical Use and Importance: High – Shows an overview of all windows devices regarding their antivirus sensor and the windows version. Metrics of interest include:
- Windows Version – Monitor the different Windows versions and suggest upgrades on devices which fall behind the pack. If windows versions appear to be lagging behind, remediation in accordance with the Defender Vulnerability Management Procedure may be in order.
- Antivirus Modes – Monitor device sensor status to ensure their status. If inactive, check the device is connecting correctly to the internet or perform the Fresh Start Retaining User Data action as outlined in the Device Fresh Start Initiation Work Instruction.
- Antivirus Security Intelligence Version – Monitor that certain devices are not falling behind on their intelligence version. If identified, perform the Update Windows Defender Security Intelligence action as outlined in the Device Defender Intelligence Update Initiation Work Instruction.
- Antivirus Platform Updates – Monitor that no devices go out of specification on updates. If they do, navigate to Antivirus - Intune and home in on the Security Essentials Windows Defender Antivirus assignment and configuration.
- Recent Antivirus Scan Results – Monitor that all devices have successfully completed quick and full scans as anticipated. If a device has missed either, perform the applicable Quick Scan action as outlined in the Device Quick Scan Initiation Work Instruction or Full Scan action as defined in the Device Full Scan Initiation Work Instruction.

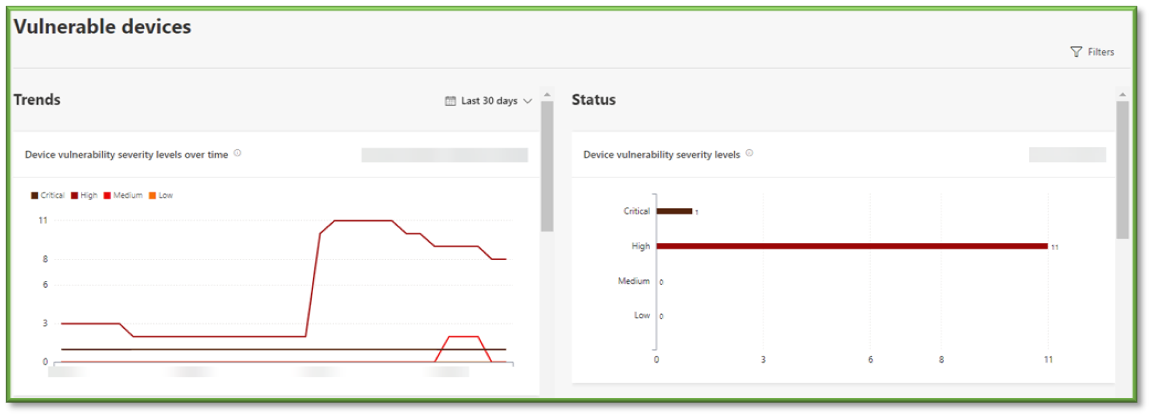
Vulnerable Devices
Description: View information about the vulnerable devices in your organization, including their exposure to vulnerabilities by severity level, exploitability, age, and more.
Practical Use and Importance: Medium – Shows an overview of what can be found in the vulnerability sections. Metrics of interest include:
- Devices with Critical Severity Vulnerabilities – Monitor the list for devices which show up as having critical vulnerabilities, which may need action following the Defender Vulnerability Management Procedure. These remediations take precedence over high and are highly recommended to be remediated.
- Applications with Vulnerabilities – Monitor the list for applications which are detected in the environment and have vulnerabilities, which may need action following the Defender Vulnerability Management Procedure.
- Devices with High Severity Vulnerabilities – Monitor the list for devices which show up as having high vulnerabilities, which may need action following the Defender Vulnerability Management Procedure. These remediations are not as severe as critical, and while it is certainly recommended that open items are closed, prioritizing assets based on their importance is sensible for this list.

Web Protection
Description: Get information about the web activity and web threats detected within your organization.
Practical Use and Importance: High (Optional) – When web filtering is leveraged, this report gives an overview of all web browsing sessions included blocked sessions. Metrics of interest include:
- Domains – Monitor to look for malicious URL’s having been accessed. If malicious URL’s have been accessed, consider following the URL Check Procedure to ensure the block is warranted. If specific websites need to be allowed or blocked, follow the Defender Web Filter URL Allow Work Instruction or Defender Web Filter URL Block Work Instruction.
- Web Categories – View an overview of how which blocks were issued for certain categories. If categories that should be allowed are not allowed, follow the Defender Web Filter Policy Modification Procedure.


Firewall
Description: View connections blocked by your firewall including related devices, why they were blocked, and which ports were used
Practical Use and Importance: Medium – Monitor events surrounding blocked inbound or outbound connections from different processes or applications trying to establish a line of communication. Metrics of interest include:
- Inbound – View all blocked inbound connections; you will be able to view the TCP/UDP port associated with the connection, the process name for the connection, the device that is being targeted as well as the remote IPs that are being utilized by the external host. If you detect any blocks on desired inbound network traffic, follow the Defender Firewall Rule Disable Work Instruction to disable the rule that is causing the block.
- Outbound – View all blocked outbound connections; you will be able to view the TCP/UDP port associated with the connection, the process name for the connection, the device that is being targeted as well as the remote IPs that are being utilized by the external host. If you detect any blocks on desired outbound network traffic, follow the Defender Firewall Rule Disable Work Instruction to disable the rule that is causing the block.
- Application – View all blocked application connections; you will be able to view the TCP/UDP port associated with the connection, the process name for the connection as well as the device that is being targeted.


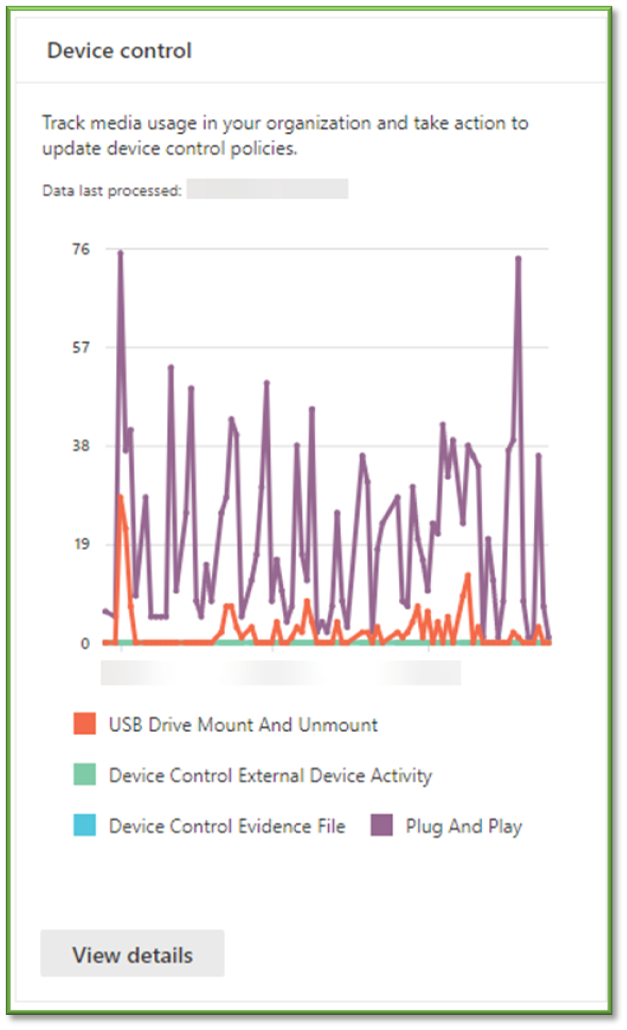
Device Control
Description: This report shows your organization's media usage data.
Practical Use and Importance: Medium – Monitor the events surrounding connecting and disconnecting devices. These can be identified as USB devices, disk drives, printers, and Bluetooth devices. Metrics of interest include:
- Device Control – Monitor the list for anomalous events, such as rapid and repeated events from a single device. If a device is identified as behaving anomalously, investigate into if recourse should be taken.

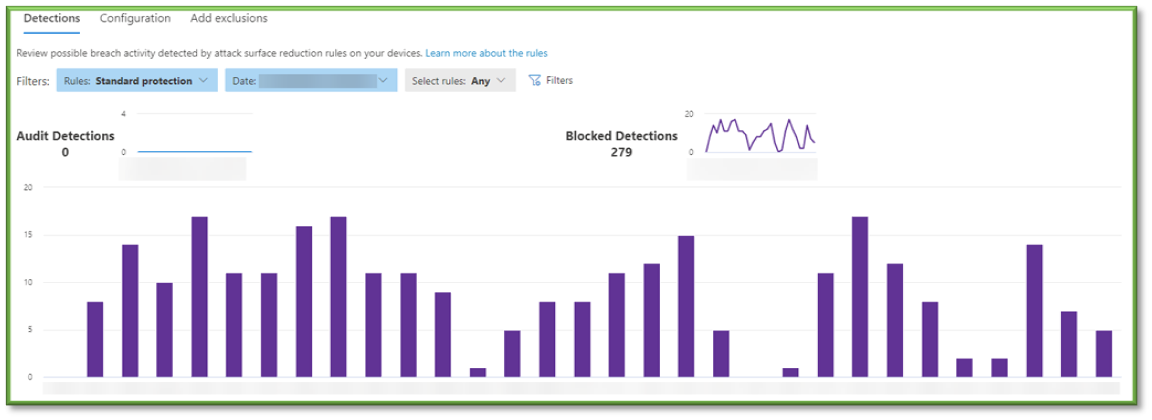
Attack Surface Reduction Rules
Description: View information about detections, misconfiguration, and suggested exclusions in your environment.
Practical Use and Importance: High – Monitor to ensure that attack surface reduction rules are not being triggered for legitimate applications. Metrics of interest include:
- Detections – Monitor the list for applications that are familiar and trusted. If trusted applications are found to be blocked by an attack surface reduction rule, follow the Defender ASR Per-Rule Exclusion Work Instruction.
- Configuration – Monitor that all devices are in the correct mode for their group membership. If devices are not in block mode that should be, navigate to Attack Surface Reduction - Intune and home in on the Security Essentials Attack Surface Reduction assignment and configuration.

You're Finished!
You should have successfully viewed the reports section of the O365 Defender portal; if any undesirable actions have been identified in a specific section, additional configuration adjusts will need to be made. For any other problems or questions, reach out to us!
